According to current reports, WordPress powers more than a third of the internet. And when you consider there are hundreds of millions of live sites today, that statistic becomes really impressive. It’s also a little scary because it means it is more likely that bad actors will tailor hacks and attacks specifically for WordPress, as there are millions of potential sites to compromise.
In fact, 94% of hacked websites we cleaned last year ran on WordPress, a statistic highlighted in Sucuri 2019 Hacked Website Threat Report. It not only looks at WordPress security but at the threat landscape as a whole. The next CMS to come close as Joomla, at just 2.5%.
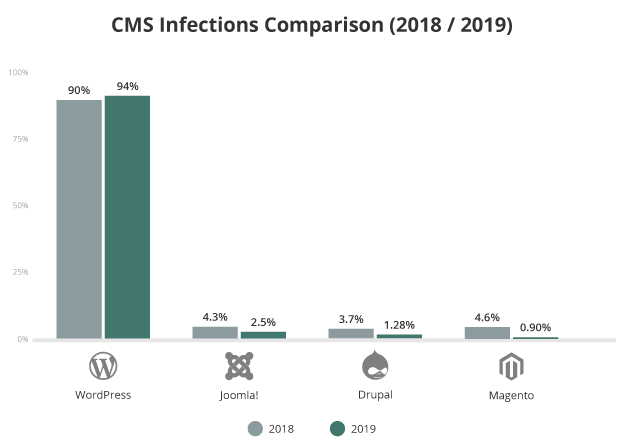
That’s not to say the fine folks at Automattic are making an insecure product. Rather, WordPress is so awesome and lets you do so much, the expanded functionality can also present an array of new attack vectors via installations, themes, and plugins.
But first things first. Let’s work on understanding what threats impacted WordPress websites last year, in order to lay the foundation for a secure 2020.
Don’t click that link! SEO spam & WordPress
As in previous years, SEO spam proved to be the most common infection for WordPress. We saw 62% of websites had an SEO spam infection during the cleanup, an increase of over 51.3% compared to the previous year.
<blockquote>Symptoms of an SEO spam infection are content on a website that seems to promote something unrelated to the purpose of the site, often links or banners ads for pharmaceuticals, designer accessories, or online casinos — to name just a few. </blockquote>
While this content is often public-facing and designed to lure away visitors, last year we found SEO spam most often targeted WordPress databases. And in those databases, we found more than one infection, with 12 different ones on average.
Backdoors on WordPress and all other sites
The 15% reinfection rate of SEO spam we saw last year, hints towards the second most common type of malware — reinfections caused by a backdoor. In fact, we discovered backdoors in about 47% of all hacked sites we cleaned up.
Hackers leave backdoors at the websites after the first infection in order to regain access to the site for reinfection. While backdoors were down compared with the number from the prior year (68% in 2018), they remain a threat that needs attention.
Among the backdoors our team found in 2019, uploaders were the most popular at 20%, followed by remote execution via POST requests at 13%, and GET requests and webshells both coming in at 6%.
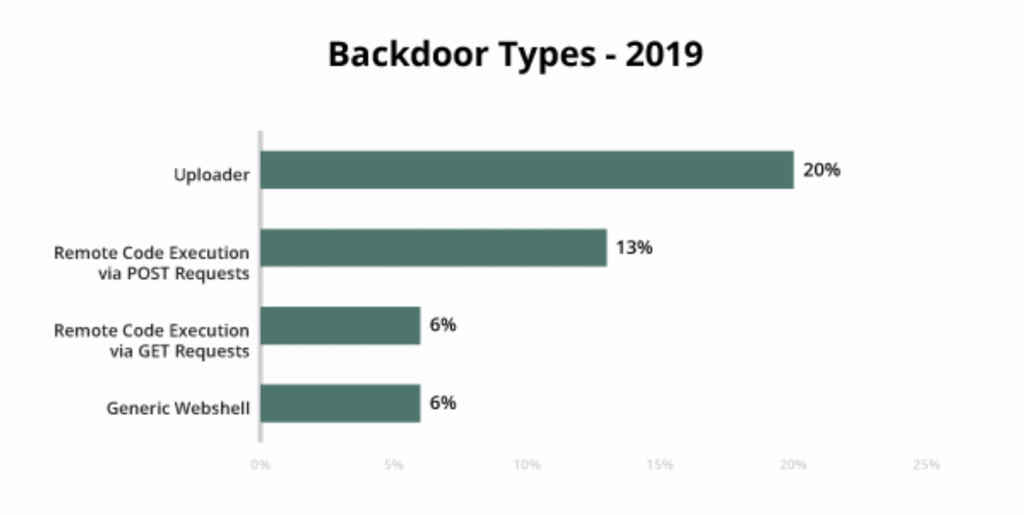
WP-VCD a source of continued infection
The WP-VCD infection comes from pirated themes or plugins installed by a site owner, and these infections were among the most common in 2019. This malware was particularly notable to us because we saw a 40% reinfection rate, with our team cleaning a total of about 5,000 WP-VCD infections.
WordPress less likely to be out of date
While we saw about the same number of out-of-date CMS installations across all platforms, WordPress users demonstrated more awareness of this important aspect of website security. Compared with other outdated platforms, WordPress came in significantly lower at 49%.
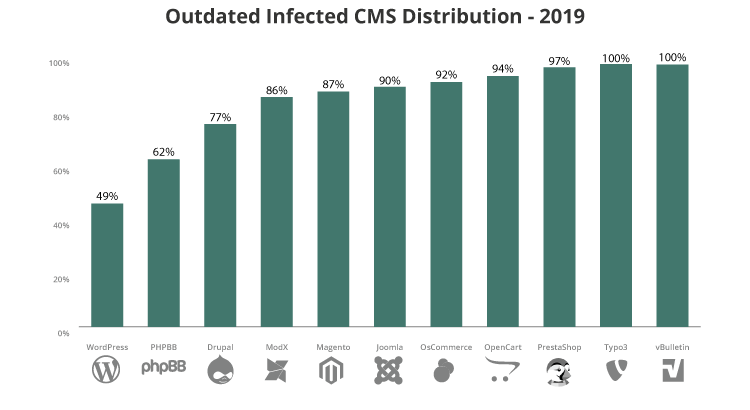
This could be due in part to the release of automatic background updates in WordPress 3.7, which gives site owners an advantage over a CMS that doesn’t run the auto-update feature.
Convenience vs. risk with update_option()
As we just discussed, update_option() affords a great deal of convenience for WordPress site owners. However, last year one of the most common bug exploits we saw were attacks targeting this function.
Legitimately used, it can update the options database table. However, without permissions configured, bad actors can gain admin access or inject data.
It’s worth attention for any WordPress site owner. Several plugins allow admin users to edit update_option(). And a lack of security checks let attackers edit internal options in WordPress. As always, this can be mitigated by updating plugins, themes, and other third-party components.
The top five plugins we saw impacted by this campaign were:
- Wp File Manager (500,000 installations)
- Easy WP SMTP (400,000 installations)
- Freemius Library (Multiple plugins are affected; about 200,000 installations)
- Newspaper and other old tagDiv Themes (100,000 installations)
- WordPress GDPR Compliance (100,000 installations)
Preventing WordPress website hacks in 2020
Despite all of the dire topics we just covered, WordPress makes securing your site a manageable process. At a bare minimum, make sure to implement the following website security measures:
- Password strength — A password manager like LastPass generates and stores complex, unique passwords.
- Login limits — Enable two-factor authentication (2FA), limit login attempts, and use a pre-login CAPTCHA.
- Audit themes and plugins — Check to make sure any themes or plugins you use are still updated and in use, and remove them if not.
- Manage your user accounts — Replace the default admin account with a unique username for making it harder to guess into your site.
- Principle of least privilege — Use roles as intended to only give access to the users who need it, for only as long as necessary.
Here’s to a more secure WordPress site in 2020
With the information and website security measures outlined above, WordPress site owners have a big head start on a secure 2020. However, some folks might prefer an even more robust approach. For them, it would be wise to bring in third-party security measures.
We encourage any owner of a WordPress site to mind their due diligence. Take a look at the website security market, and check compatibility as well as layers of protection (our own Website Security Platform handles both).
Whatever route you choose to go, we hope the upcoming year sees a secure WordPress site enabling your success, After all, safer internet for everyone is what we’re all about.
Photo by Georg Bommeli on Unsplash

Jakiwatsonn
What are your thoughts on plugins like iThemes Security Pro, WordFence Pro and Sucuri? I know they all slightly differ in terms of their security features and products, but was interested in knowing if you have used these and would recommend them?
Jim
Thanks for this useful article. WordPress security is very important. I always use the latest version of WordPress(plugins and themes). Also, I changed the login URL and usually change login details.