There are over 27 million live WordPress websites. While it’s awesome to be part of such a large, active community, the Content Management System’s (CMS) popularity also makes it a prime target for Cross-Site Scripting (XSS) attacks.
Fortunately, just because hackers focus on WordPress doesn’t mean their breach attempts are destined to succeed. By using the right tools and techniques, you can harden your site against XSS attacks.
In this post, we’ll discuss what XSS is and why WordPress is uniquely vulnerable to these kinds of intrusions. Then we’ll share four strategies that you can implement to help protect your site against them. Let’s get started!
An introduction to XSS attacks
An XSS attack occurs when a hacker exploits a vulnerability on your website and attempts to inject unauthorized JavaScript code. The malicious script is then executed on either the client-side in the browser, or is stored and carried out on the server.
XSS attacks are often designed to collect data from your visitors, such as their passwords or payment information. However, the attacks can also change how your site looks or functions. For example, cybercriminals might redirect your users to an entirely different website.
This kind of redirect may result in your traffic plummeting, as the hacker steals 100 percent of your visitors. The rerouting can also be a launchpad to further attacks. For example, a nefarious redirect may send your traffic to a scammy website.
Some bad actors may even mimic your site, in an attempt to trick your customers into sharing personal information and payment details. This can be particularly disastrous for your reputation.
XSS attacks are a huge problem for many different CMSs. However, WordPress is uniquely vulnerable because many websites on the platform use plugins. These extensions add code to your site, which may introduce XSS vulnerabilities that hackers can exploit. In its 2021 report, WP White Security discovered almost 4,000 known WordPress plugin vulnerabilities, including ones that could result in successful XSS attacks.
With so many loopholes to exploit, it’s perhaps not surprising that Wordfence identified 330 million attempted XSS attacks in 2020. With cybercriminals actively trying to leverage known and unknown weaknesses, it’s important to do everything you can to protect your website.
How to protect your WordPress website against XSS attacks (4 key tips)
XSS may be one of the most common methods hackers use to infiltrate websites, but there are ways to bolster your site’s security. Let’s look at four techniques that you can implement today.
1. Keep up-to-date on the latest vulnerabilities
By continuously monitoring your themes and plugins for known weaknesses, you can maximize your chances of discovering problems early. Then you can take steps to address these security loopholes before hackers have a chance to exploit them.
WPScan maintains a Vulnerability Database of known WordPress Core, theme, and plugin vulnerabilities. It has also released a WPScan plugin that lets you scan all your plugins for known risks:
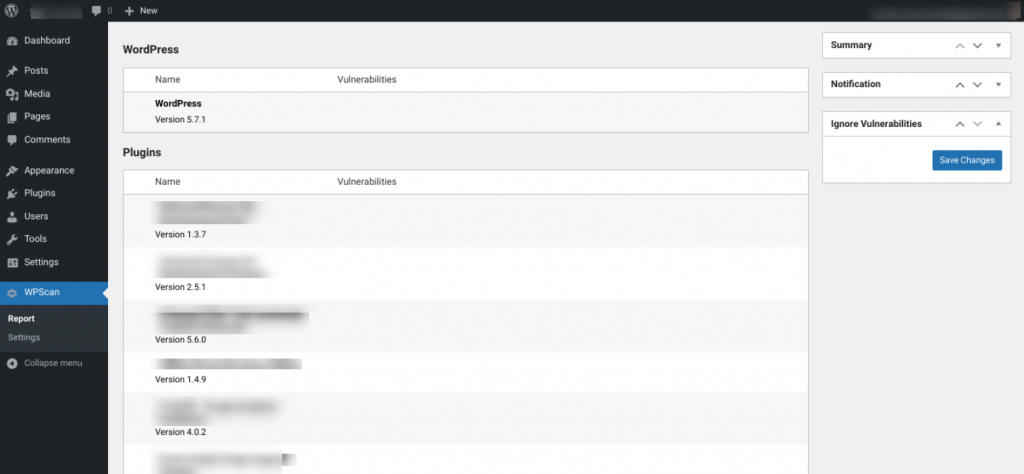
However, if you’re a ManageWP customer, you don’t even need a separate plugin. We’ve collaborated with WPScan to showcase all its data directly inside your ManageWP dashboard.
Vulnerability Updates displays a notification alongside any plugins that have known vulnerabilities. This makes it easy to identify issues that may be currently putting your site at risk:
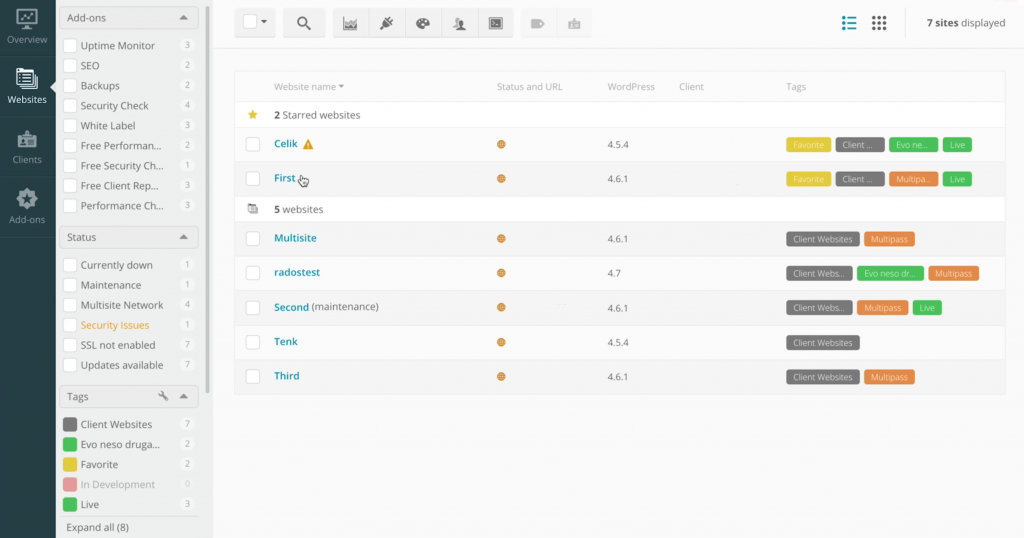
If you discover a vulnerability, the safest solution is to deactivate and then delete the plugin in question. However, this may not be possible if the extension delivers a crucial feature to your website.
In that case, you can check to see whether the developer has issued a patch, as a responsible creator should be eager to fix any security issues. If an update is available, resolving the weakness may be as simple as clicking on Update Now:
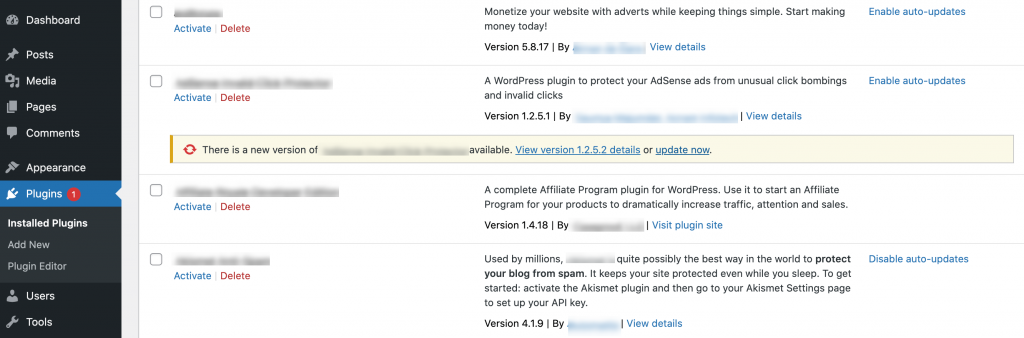
However, sometimes you may need to continue using unsecured software, such as when the developer is still creating a patch. Until you can install that update and close the vulnerability, it’s smart to be extra vigilant for any signs that your site is under attack. This could include monitoring your site for downtime, watching for a drop in performance, and adding the ManageWP Security Check feature to your site so you’ll be notified about any issues immediately.
2. Use a Web Application Firewall (WAF)
A Web Application Firewall (WAF) filters out malicious requests, including XSS attacks, before they have a chance to reach your website. There are various WAFs that you can use with WordPress. Sucuri WAF is a popular option:
After purchasing a Sucuri WAF plan, log into your account and click on Protect My Site Now. You can then enter the domain name you want to protect, and specify whether you want to whitelist any directories.
Hackers are known to deliberately target vulnerable parts of websites, such as admin directories. By restricting access to these sensitive areas, you can further reduce the chances of falling victim to a successful XSS attack.
After entering your domain, you’ll need to scroll to the general dashboard page. There, you’ll find Sucuri’s DNS information. Your next task is to change the IP address for your website’s A record so that it points to Sucuri’s firewall.
You’ll typically make this adjustment by logging into your domain registrar or Domain Name Server (DNS) provider’s account. This step will vary depending on how your account is set up. If you’re unsure how to make the change, you can check your provider or registrar’s documentation for more information.
DNS changes may take up to 48 hours to propagate, so you might need to wait for this update to come into effect. You can verify whether your DNS has propagated by visiting whatsmydns.net.
3. Add an HTTP security header
Every time someone visits your site, the server reacts with HTTP response headers. These headers tell web browsers how to act throughout their interactions with your website, such as when managing the cache.
You can help protect your site against XSS attacks using the X-XSS-Protection header. With this header in place, your website will prevent the page from being loaded when an XSS attack is detected, which can safeguard your site against certain categories of XSS breaches.
You add this security header to your site’s .htaccess file, which is a configuration file that tells your server how to handle various requests. After connecting to your site using your favorite File Transfer Protocol (FTP) client, open the .htaccess file and add the following:
<IfModule mod_headers.c> Header set X-XSS-Protection "1; mode=block" </IfModule>
When you’re done, you can save your changes and close the file. Your website will now prevent the page from being loaded whenever it believes that an XSS attack is underway.
4. Add a Content Security Policy (CSP) header
A Content Security Policy (CSP) can help mitigate XSS attacks by specifying which resources (scripts, styles, images, etc.) are permitted to load. By whitelisting authorized sources, you can stop browsers from loading malicious content.
Unfortunately, there isn’t a one-size-fits-all approach to CSPs. You’ll need to evaluate the resources you’re actually loading and consider how to manage them effectively. Then you can create a policy based on your specific requirements.
When developing a CSP, you’ll use default-src to specify the standard policy for loading content such as images, fonts, media, and AJAX requests. You can also define legitimate JavaScript sources using script-src, legitimate image sources using img-src, and authentic stylesheet sources using style-src.
Below is an example of what defining a valid source of images looks like:
img-src 'self' img.example.com;
For more information on constructing a CSP header, you can check out the Quick Reference Guide.
Once you’ve created your CSP, the next step is to add it to your functions.php file. In the WordPress dashboard, navigate to Appearance > Theme Editor:
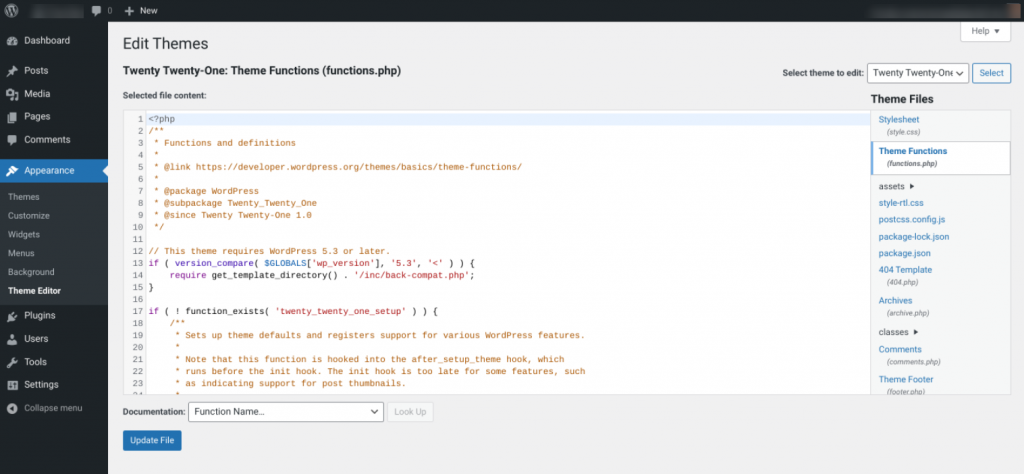
To the right of the screen, select the functions.php file and add your CSP header. When you’re done, click on Update File.
Conclusion
XSS is a common attack that has the potential to destroy your reputation as a reliable, security-conscious website. The good news is that there are ways to protect both your site and your visitors from this type of data breach.
Let’s recap four practical steps that can greatly minimize your chances of falling victim to an XSS attack:
- Keep up to date on the latest vulnerabilities.
- Use a firewall such as Sucuri WAF.
- Add an HTTP security header by adding code to your .htaccess file.
- Add a CSP header by editing your functions.php file.
Do you have any questions about protecting your site against XSS attacks? Ask away in the comments section below!
Image credit: Unsplash.

0 Comments