Welcome to the third installment of our series dedicated to everything WordPress security. It is my hope that by the time you finish reading this collection of posts, you’ll have a clearer idea of how to set up proper security protocols for your site and maintain them as the CMS undergoes updates and modifications.
I want you to be a security pro by the end of this! Okay, so maybe not a pro, but you should definitely have a handle on the most important bits!
Here’s a handy table of contents list for you in case you missed a previous post or you want to skip ahead:
- Part 1: Installation
- Part 2: Updates
Part 3: Management & Logins- Part 4: Security & Backup Plugins
- Part 5: Roundup
In today’s post, I’ll be exploring how to maintain security on a site that’s been live for a while and how to better manage logins. We’re going beyond the “pick a complicated password” style tips here to delve into a bit more of the nitty gritty stuff. You ready?
Limit Logins
One of the first things you can do to manage WordPress security is to limit the number of times people can try to login. As I mentioned in a previous post, many hackers use brute force attacks to try to crack your username and/or password. Even if these attacks don’t succeed, the repetitive nature of the attacks can put a significant load on your server.
By limiting logins, you prevent a hacker from even attempting a brute force attack. He’d get to try two to three times then have his IP banned. You can easily set this up by using the Limit Login Attempts plugin, according to Ryan Burr, a technology service expert, and WordPress developer with One Stop Tek Shop. This plugin hasn’t been updated in over two years, however, so while its features are great, you might want to pass on it for fear of opening yourself up to additional security vulnerabilities.
I recommend instead, Login Lockdown. Since both of these plugins let you limit the number of failed login attempts a user can make before his IP is banned for however many hours you determine, “brute force attacks would be much harder to pull off,” says Burr. “The hacker would need to have many different proxies because the plugin would keep banning that IP address after a certain number of failed login attempts,” he says, noting that you can customize a variety of settings here to create the optimum security configuration for your site.
Ban Users Who Attempt to Use Admin as Username
It’s one thing to make sure you don’t use admin as a username. It’s another altogether to prevent other people from trying to login with it. Since “admin” has such brute force attack connotations these days, random people that try to login to your site with it are often hackers. You can halt their attempts in their tracks, however, by banning anyone who tries to use “admin” to login, says Damon Burton of SEO National.
 He suggests using Wordfence to set up this auto-ban feature. Of course, this plugin includes a lot of other features, too like two-factor authentication, blocking of known attackers, and more. I’ll talk more about this plugin in our next installment.
He suggests using Wordfence to set up this auto-ban feature. Of course, this plugin includes a lot of other features, too like two-factor authentication, blocking of known attackers, and more. I’ll talk more about this plugin in our next installment.
Establish the Correct File Permissions
Another thing you want to do is establish the correct file permissions on your site. According to WordPress.org, setting a directory with permissions of 777 could allow a hacker or some other malicious entity to edit your files or even upload new files—like malware. Your wp-config.php file should be set to 600; your regular files should be set to 640 or 644; and your directories should be set to 750 or 755. While you don’t have to make this change on every host, you should still look into it via WordPress’ guide to Changing File Permissions.
Create an .htaccess File
If you want nice permalinks on your site, you’re going to need an .htaccess file anyway. But adding one can actually beef up your security a bit. Again, it’s not a total solution on its own but it does work well in tandem with other methods.
Burr suggested a great tutorial for creating an .htaccess file, I feel compelled to link to here because it’s so comprehensive, plus it offers a downloadable .htaccess file you can start using on your site immediately. Once you follow its basic setup instructions, you can block access to certain files in your WordPress directory. If people can’t load these files—either directly or indirectly—the files can’t be tampered with. To “harden” your WordPress installation, you’ll need to add a few lines of code to block access to a few specific files, including:
- wp-config.php
- readme.html
- license.txt
- wp-includes directory
Beyond blocking access to specific files, you can also block access to file types. Typical file types to block include backups, config, txt, and log files. Basically, anything that’s used on the backend for design, development, or documentation should be blocked.
If you want to block access to specific plugin or theme directories or any other directories on your site, you can block the whole directory, too. This is a smart move to do for any directory that doesn’t have an index file. Directories without index files will list out all of the pages and files contained within it when accessed. It’s giving hackers information they don’t need, so hide them!
Hide the Login Page
This is another .htaccess modification but it’s a little bit different than the others so I thought it deserved its own subheading. You can deny access to the login page for your WordPress site altogether. Of course, this only works if your site has a single author and that author’s IP address hardly ever changes. Another few lines of code in the .htaccess file will deny access to the login page to everyone but the IP addresses you specify.
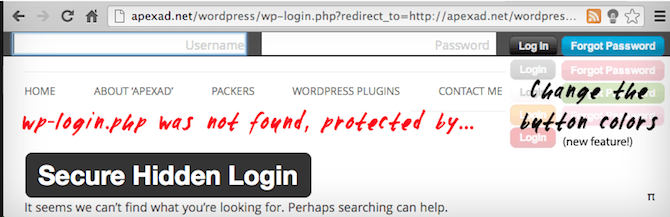 If you want to keep your options open in terms of adding authors to your site later, you can always use a plugin to simply hide the login page from unauthorized users. Secure Hidden Login is one such option. While you can set it up so the login screen appears when the “WordPress” logo is clicked, a more secure option would be to set keyboard activation. So, someone goes to your website’s wp-login page only to find nothing there. She could activate the username and password fields by pressing a key combination.
If you want to keep your options open in terms of adding authors to your site later, you can always use a plugin to simply hide the login page from unauthorized users. Secure Hidden Login is one such option. While you can set it up so the login screen appears when the “WordPress” logo is clicked, a more secure option would be to set keyboard activation. So, someone goes to your website’s wp-login page only to find nothing there. She could activate the username and password fields by pressing a key combination.
Remove Generator Tag Info
Hackers do all kinds of things to try to get into WordPress sites, one of which is running scripts to find WordPress installations across the Internet based on footprints. “Footprints are identifiable or recurring lines of text or code that would identify that a site uses a particular set of code,” says Burton. WordPress is one such example of “recurring lines of text or code.” Plus, WordPress by default identifies that the site you’re looking at was built on WordPress.
A WordPress site’s source code will say something like this, says Burton:
<meta name="generator" content="WordPress 3.8.4" />
You can remove this tag from your source code, however, which gives hackers one less thing to find (and target) your site by. “Webmasters can add the following line of code to their functions.php file:
remove_action('wp_head', 'wp_generator');
According to Burton, removing the generator tag means your site no longer identifies itself as WordPress.
Enable Two-Step Authentication
Another thing you can (and should) do to protect your site is to set up two-step authentication. By requiring your site users to take two steps to login, it discourages brute force attacks and most hackers in general. Your site would be perceived as just too difficult to crack, which is definitely a good thing!
There are several plugins out there that enable this feature on your site. A few particular favorites include:
- Clef: Once set up, all you have to do is open the Clef app on your mobile phone and focus its camera on a moving image on your computer screen. It’ll “lock” in place and you’ll be logged in.
- Duo Two-Factor Authentication: After inputting your password via the normal login form, you’ll have to complete a secondary step to login, like confirm it on a phone app, in a SMS text message, or in a phone call.

- ManageWP: Yes, we offer two-factor authentication, too. After logging in like normal, you’ll have to confirm the login by entering a verification code that is sent to you via email or SMS text.
Conclusion
Managing security on your WordPress site and configuring logins to be as locked down as possible will take some time. But once all of these measures are in place, you site is going to be a lot more reliable to its users. And you’ll have the peace of mind that a malicious takedown is unlikely. All good things!
Do you use any of the aforementioned security methods? Do you do anything else that falls into the realm of management and logins? I’d love to hear your thoughts below! And be sure to check back again next week for the fourth installment of our security series. Until then!
Leave a Reply