As a WordPress user, safeguarding your site from security attacks should be of the utmost importance. WordPress powers nearly 35 percent of the internet, making it a major target for cybercriminals.
Taking the time to learn the ins and outs of the most common types of cyberattacks can help. When you know what you’re up against, it’s easier to implement a comprehensive security strategy.
In this post, we’ll discuss the eight most common security attacks and how they work. Then we’ll share some tips and tools to help protect against them. Let’s get to it!
8 types of security attacks and how to prevent them
A security attack is an unauthorized attempt to steal, damage, or expose data from an information system such as your website. Malicious hackers can go about this in a variety of ways, including the ones listed below.
1. Malware
Malicious software – ‘malware’ – infects devices without users realizing it’s there. Variations include Trojan horses, spyware, ransomware, ‘malvertising’, and viruses.
Secretly infected files or software can further introduce malware to your site. You could also trigger a malware download by clicking on a link in a pop-up window or an email attachment.
To prevent malware infections, you’ll want to install a security scanner. This tool will alert you to otherwise undetected problems on your site. Our own security scanning feature, powered by Sucuri, is a low-cost and highly effective choice:
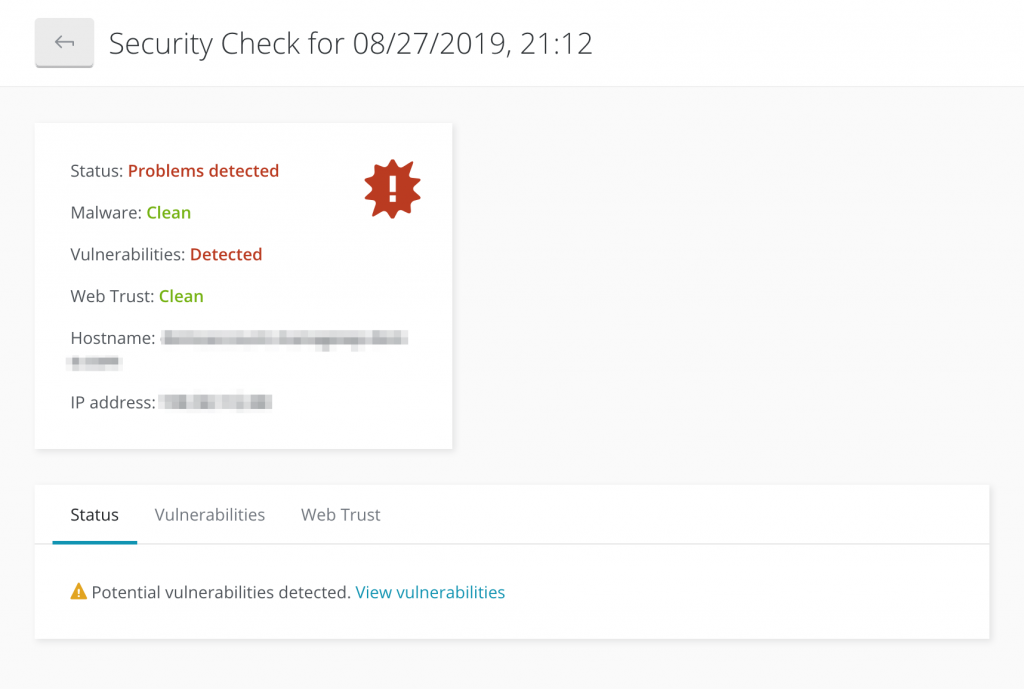
In the event your server is compromised, you can restore your files from a backup. Tools such as our ManageWP Backup feature enable you to schedule copies and save them to an external destination. This way you’ll have one handy should your site become compromised.
2. Drive-by downloads
A drive-by download is a method of distributing malware, and occurs when a malicious script is inserted into a page’s PHP or HTTP. When a person visits the infected site, the malware is downloaded onto, and silently infects, the device.
These threats can be tricky because they’re not attributed to human error. You could visit a seemingly legitimate site, unaware it’s been compromised.
Therefore, the best action you can take to prevent drive-by download attacks is to keep your security systems updated and remove any unnecessary software. You might also consider using an ad blocker, such as AdBlock:
This is a Chrome extension that prevents ads on static web pages and video websites. It is free to use and customizable, but is by no means the only option available.
3. Phishing
Phishing is among the oldest and most common types of security attacks. What’s more, these attacks have increased by 65 percent in the last year, and account for 90 percent of data breaches. This form of social engineering deceives users into clicking on a link or disclosing sensitive information. It’s often accomplished by posing as a trusted source via email.
Another approach is ‘spearphishing,’ which is a targeted attack on an individual. A high-profile example is the 2016 case of Hillary Clinton. Staff members were tricked into sharing sensitive information and credentials which led to stolen data.
Since phishing relies on human error, training users to properly vet emails is critical. To further minimize risk:
- Never click on or download a file that seems suspicious.
- Be wary of emails addressed generally, such as to “Dear Friend” rather than to you specifically.
- Notice any glaring spelling or grammatical mistakes in emails.
These are particularly important to pay attention to when an email is asking for payment or personal information.
4. Brute-force attacks
In brute-force security attacks, hackers often use dictionary software to repeatedly and systematically attempt password combinations until they find one that works. Once the cybercriminal has access, they can wreak all sorts of havoc on your site.
Users should always choose strong passwords that include a combination of letters, symbols, and numbers. You might consider using a password generator tool such as LastPass:
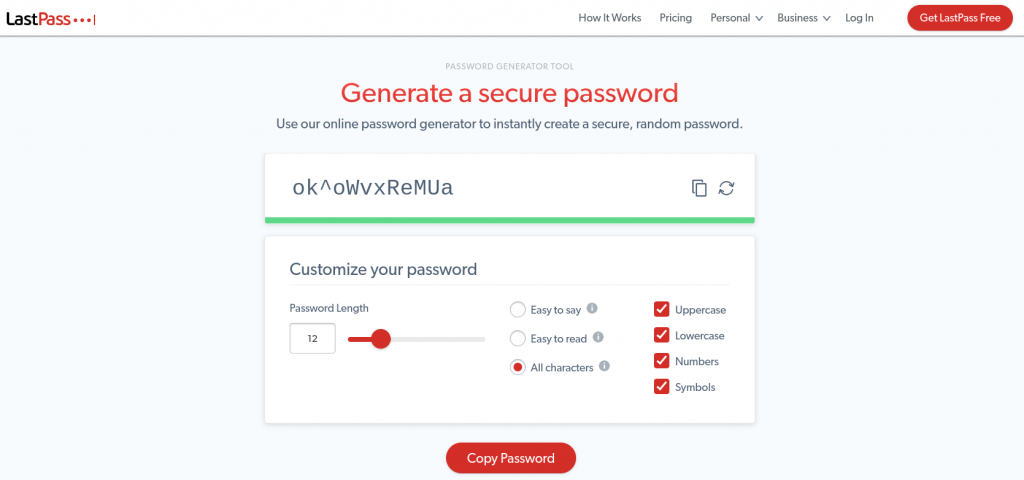
This tool enables you to quickly generate a secure combination of characters. It’s also useful for safely storing passwords across devices so you don’t have to worry about forgetting them.
You could also help prevent brute-force attacks by limiting login attempts and implementing Two-Factor Authentication (2FA). If a cybercriminal does gain access to your site, you can block them from retrieving confidential information by further password protecting sensitive files.
5. SQL Injections
Structured Query Language (SQL) injections are when an attacker injects malicious code into a server to manipulate back end databases. The goal is to reveal private data such as user lists, customer details, and credit card numbers.
SQL injection attacks can cause severe damage to businesses. Attackers can delete tables and gain administrative rights, although the most devastating aspect is the loss of your customers’ trust and loyalty.
To prevent malicious code from infiltrating your database, you can use a Web Application Firewall (WAF), which acts as an additional protective barrier. GoDaddy offers a WAF in their Deluxe and Express Website Protection plans.
Injections can occur through any form element on your site, including contact forms, blog comments, and search bars. Therefore, it’s important to review your forms to ensure each field is configured for the correct entry type. For example, a name field should only allow alphabetical entries.
WordPress also suggests sanitizing form fields. Using the sanitize_text_field() function automatically rejects any risky entries in your forms.
6. Man-In-The-Middle (MITM) attacks
With MITM attacks, the criminal positions themselves between your device and the server. They eavesdrop on, intercept, and manipulate communication between two parties – this often happens on unsecured wireless networks such as public WiFi.
Detection of these attacks is difficult, but prevention is possible. Always use secure WiFi connections, and consider investing in a Virtual Private Network (VPN).
It’s also wise to install a Secure Sockets Layer (SSL) certificate on your site. This ensures communication between your website and a visitor’s browser is encrypted and inaccessible to MITM attackers. You can acquire an SSL certificate through a provider such as GoDaddy:

Installing an SSL certificate is a straightforward task, and gives you not just peace of mind, but absolute protection from malicious MITM attacks.
7. Denial-of-Service (DoS) attacks
In a nutshell, a DoS attack sees an attacker flood a website with an overwhelming amount of traffic, often using ‘bots.’ As a result, the system crashes and denies access to real users.
These attacks are growing increasingly popular. Hackers can take advantage of vulnerabilities in connected devices and use them to launch Distributed Denial-of-Service (DDoS) attacks.
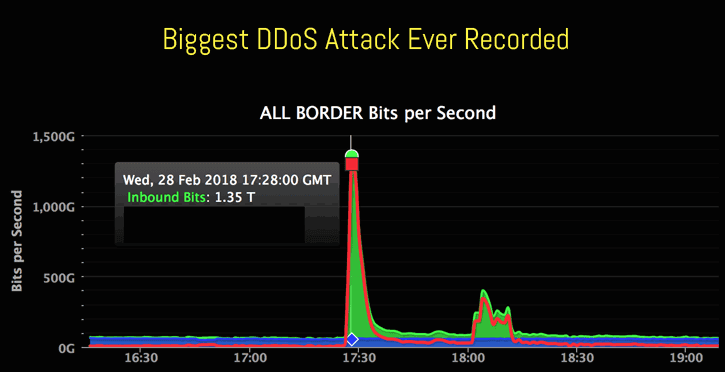
For example, GitHub experienced a noteworthy DDoS attack in 2018. As they explained, the attack consisted of more than “a thousand different autonomous systems (ASNs) across tens of thousands of unique endpoints.” With traffic hitting at 1.35 terabytes per second, it’s the largest DDoS attack to date:
To minimize your site’s risk of DoS attacks, it’s important to constantly monitor your site’s traffic, and have dependable tools to mitigate the negatives. For example, routers and WAFs can block suspicious visitors, while your server needs to be strong and stable. What’s more, it’s smart to update these tools regularly.
8. Cross-Site Scripting (XSS)
Cross-Site Scripting (XSS) attacks occur when an attacker exploits vulnerabilities in a web application by injecting malicious code – usually JavaScript – into the user’s browser. This lets them gain control of (and access to) the user’s browser, as well as account credentials and sensitive data.
One step you can take to prevent XSS is to add a Content Security Policy (CSP) header to your functions.php file, which whitelists authorized sources. The process takes a few steps to implement, but is worth it for the extra layer of security. You could also do this via your .htaccess file.
However, there are there are other important methods of XSS prevention you could implement. For example, you could enforce passwords for sensitive pages, and implement validation through classification or input sanitization.
How to prevent cyberattacks on your WordPress site
There are many precautions individuals and businesses can take to prevent security attacks, including those mentioned throughout this post. Unfortunately, even the most cautious can fall victim to security attacks. That’s why early detection and prevention are key to safeguarding your WordPress site.
Our platform makes it easy to be proactive about your site’s security. ManageWP’s Sucuri Security Checks and Vulnerability Updates can keep you informed about any suspicious activity or potential access points for hackers:
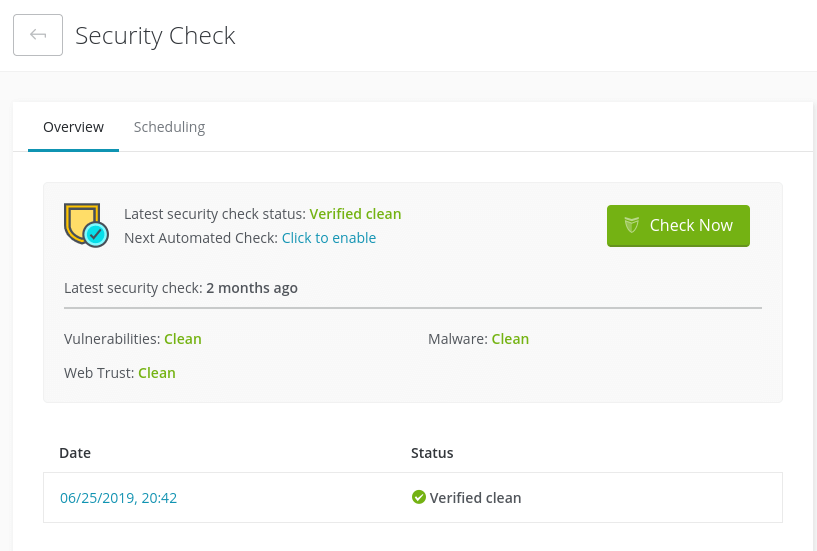
Sucuri scans can detect malware, changed files, potential vulnerabilities, and outdated software. This insight lets you act fast to resolve an issue before a cybercriminal takes advantage.
In addition to Security Checks, ManageWP features also include 2FA, uptime monitoring, and more. You can also automate your site backups and security scans to help keep your content and users safe without lifting a finger.
Conclusion
Cyberattacks pose a growing threat, especially for WordPress users. Understanding the common types of attacks and how they work can help inform and enhance your security strategy.
As we discussed in this article, there are many different methods cybercriminals can use to infect your site, including malware, phishing, brute force, and DoS attacks. These threats require a multi-layer approach to site security. Tools such as ManageWP’s Security Checks make it easier to detect and stop attacks on your WordPress site.
Do you have any questions about preventing security attacks on your WordPress site? Let us know in the comments section below!
Photo Credit: Pexels.

Suzie
Thanks for sharing this useful information. I think content theft is also a security problem that most site owners should pay extra attention to.
David Jeson
Really Great work Man, Great Thanks for the encouragement and these actionable tips. This saved me a lot of time to find. Appreciate your efforts