There are thousands of plugins that can enhance your WordPress installation with new features. Unfortunately, they can also expose your website to hackers. In fact, almost all WordPress vulnerabilities are related to plugins.
Thankfully, you don’t have to choose between building your website without the help of WordPress’ more than 50,000 plugins or keeping it safe. By taking some simple precautions, you can reap the benefits of these tools while preventing cyberattacks.
In this article, we’ll cover seven ways that you can use WordPress plugins safely. Let’s get started!
An introduction to WordPress plugin security
There’s a WordPress plugin to help you accomplish just about any task and solve any problem related to your website. They can help you add Two-Factor Authentication (2FA) to your login page, build an e-commerce store, attract customer reviews, and so much more.
There are WordPress plugins to suit every need and budget, including:
- Security plugins such as Sucuri, Jetpack, and All In One WP Security & Firewall.
- Performance optimization plugins including W3 Total Cache and WP Rocket.
- E-commerce plugins such as WooCommerce, Easy Digital Downloads, and Ecwid.
- Membership plugins including WooCommerce Memberships and MemberPress.
- Page builders such as Elementor, Divi, and Beaver Builder.
However, even free plugins come at a cost. Extensions add more code to your website, which means more potential weak points for hackers to exploit. A study even found that 98 percent of WordPress vulnerabilities are related to plugins.
Going without plugins entirely is nearly impossible unless you’re running the simplest of blogs. Instead, the solution to this problem is to follow plugin security best practices to minimize the openings on your site that hackers might take advantage of.
7 ways to protect your website when using WordPress plugins
Thankfully, you don’t need to choose between WordPress’ huge collection of plugins and locking down your website. Here are seven tips that can help keep your content and your visitors safe.
1. Only install plugins from reputable sources
Some plugins may contain malware, viruses, and other digital threats. To help protect your website, you should only install products from reputable sources, such as the official WordPress Plugin Repository or well-known marketplaces such as CodeCanyon.
Whenever possible, we’d recommend using the official WordPress Plugin Repository. The platform has strict security guidelines for all the extensions featured on its website, so you can feel confident any tools available via this source have been thoroughly vetted.
If a security issue is discovered, then WordPress.org will work with the plugin’s developer to try and resolve this issue. If they can’t reach a resolution, the plugin may be removed from the directory, or other members of the community may take steps to patch the vulnerability themselves.
2. Research your plugins’ history and reviews
Even when you’re installing a plugin from a reputable source, you should still do your research. It’s recommended that you check the plugin’s reviews, particularly the most recent ones:
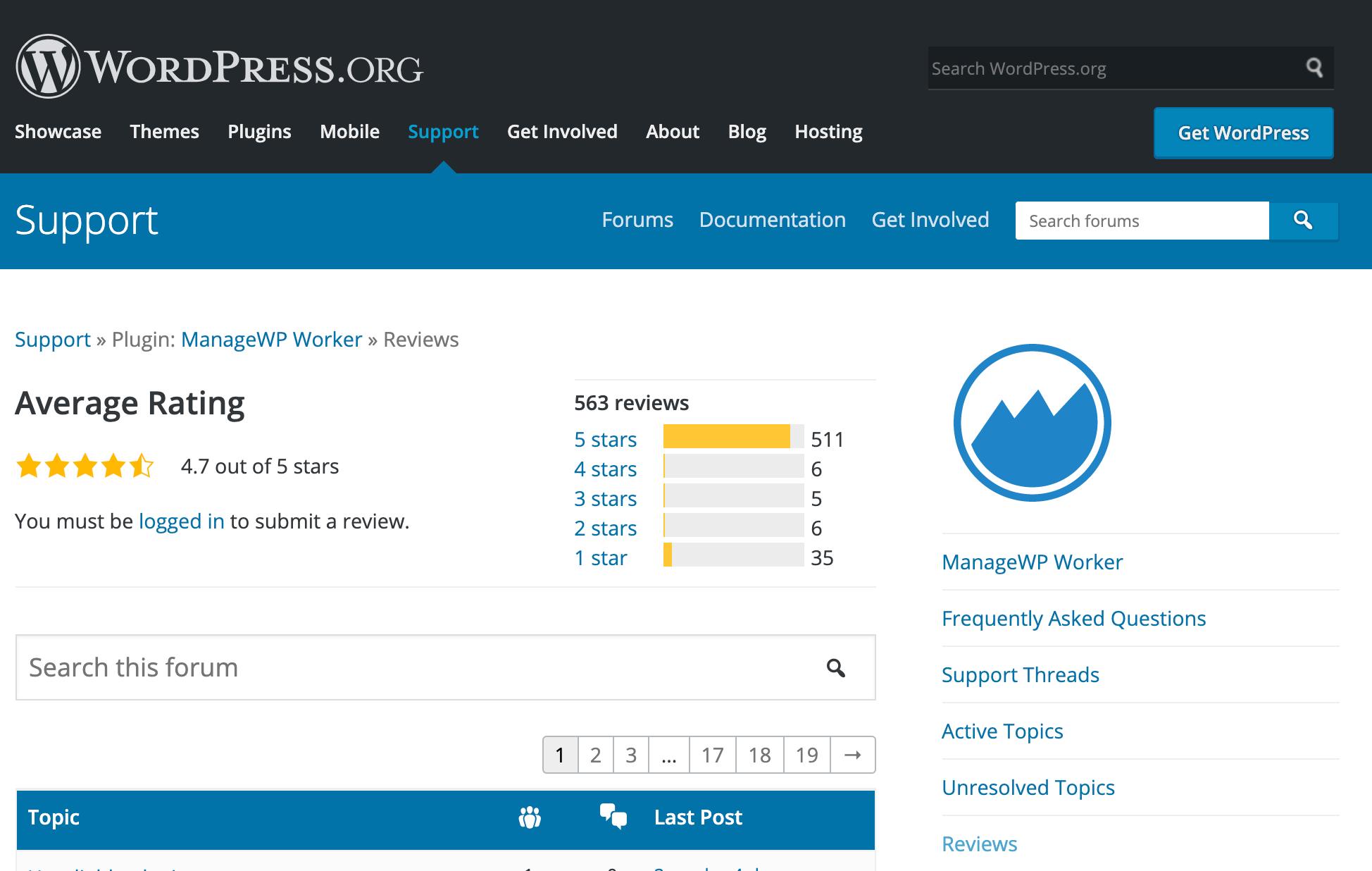
You should also check the date of the plugin’s most recent update. If the developer hasn’t released a new version in the past six months, then you may want to use an alternative, since dated code is more likely to contain vulnerabilities:
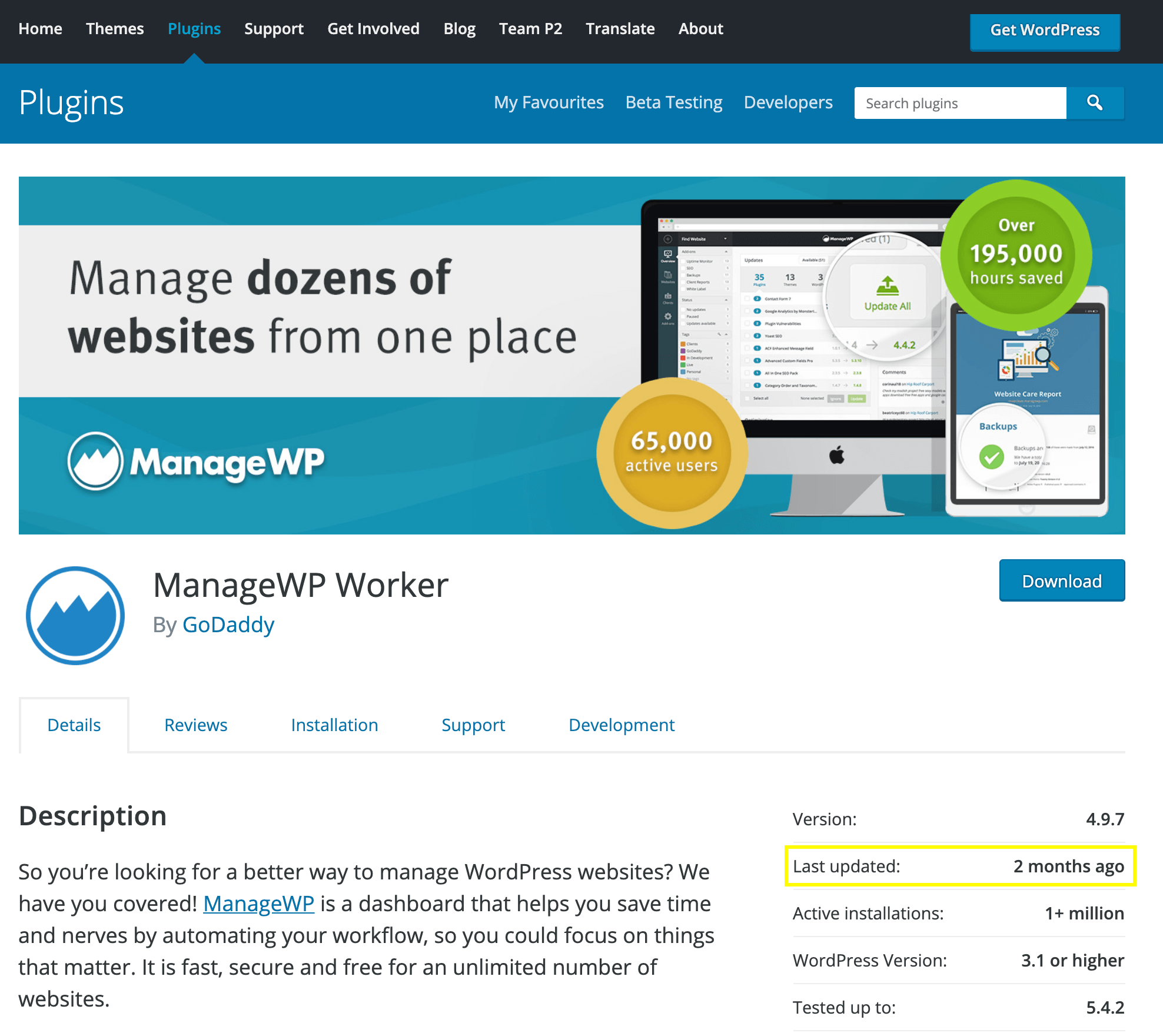
Reviews aren’t the only place where users can discuss a plugin. You can also check whether anyone is complaining about a specific tool on third-party forums or blogs. Searching popular social media platforms such as Twitter and Facebook may be helpful, too.
3. Keep your plugins up-to-date
New releases often include fixes for exploits and vulnerabilities, so it’s important to keep your plugins up-to-date. If you fall behind, then your website could be open to attacks.
To check for updates, log into your WordPress dashboard and click on Updates in the sidebar menu. You can then select each plugin’s accompanying checkbox and click on Update Plugins:
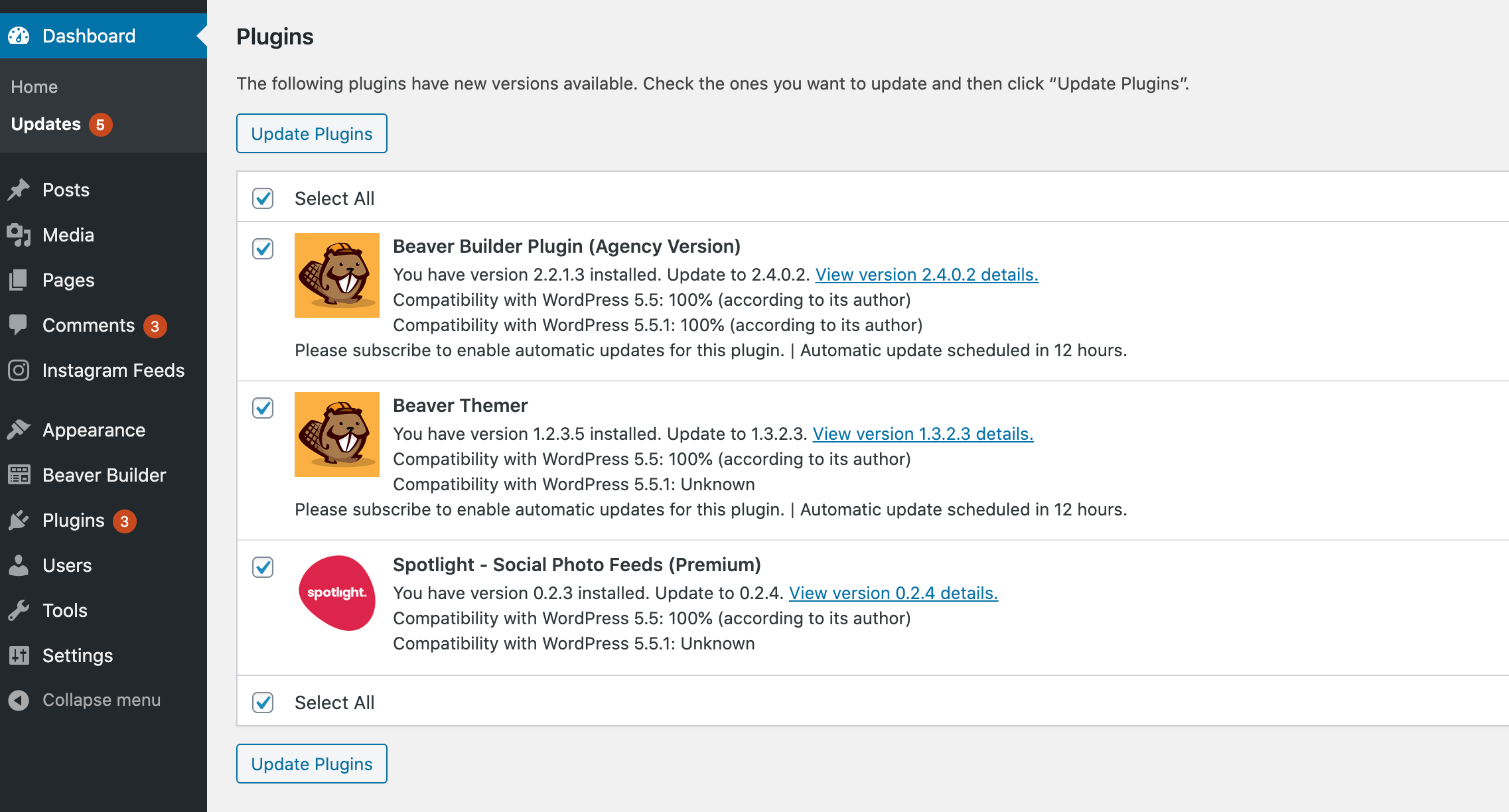
You’ll typically want to install all available updates, unless you have a specific reason not to.
Alternatively, you can log into your ManageWP dashboard and update all your plugins simultaneously, even across multiple WordPress websites:
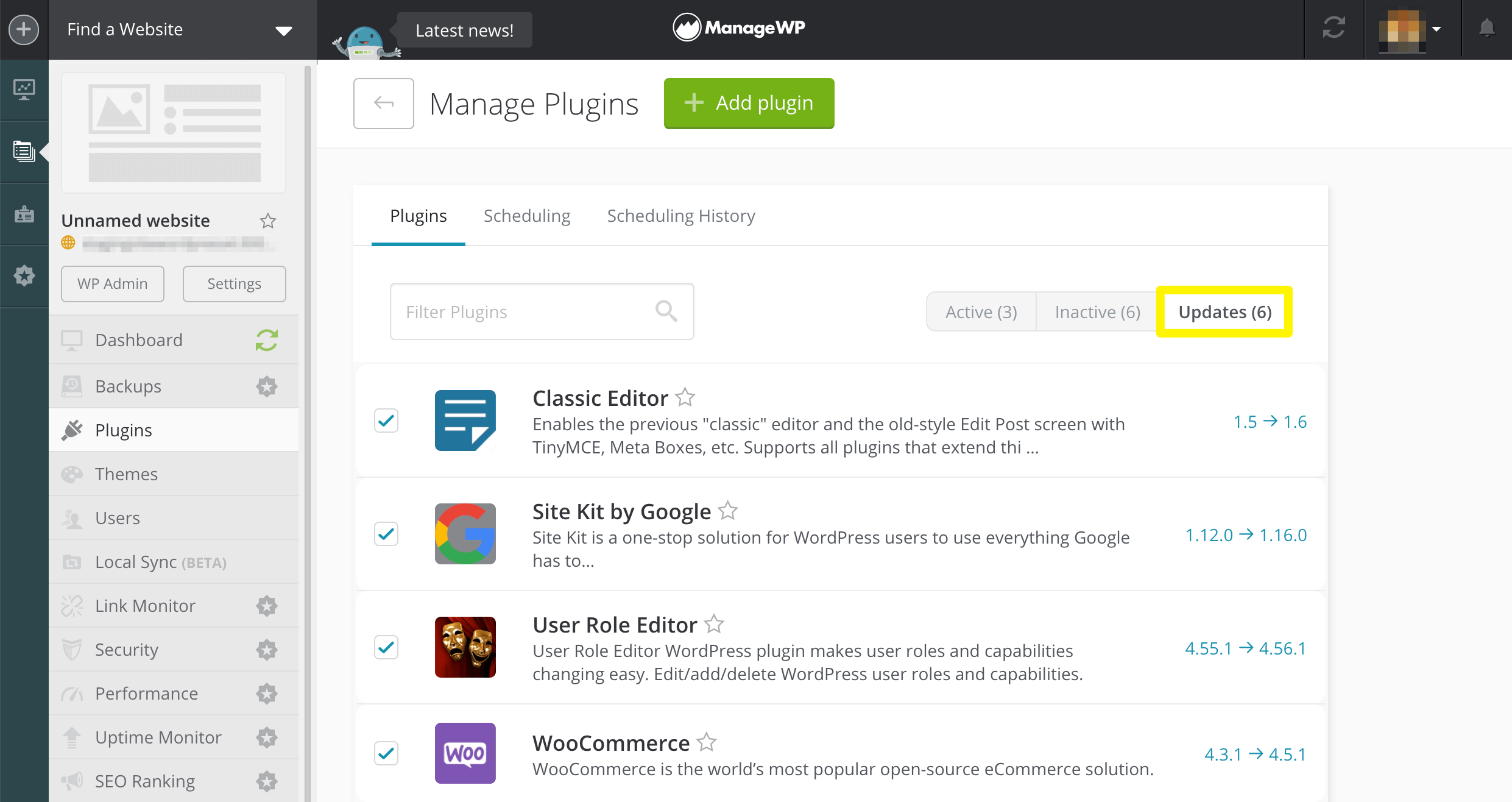
Occasionally, updating a plugin may result in a conflict, as products that previously co-existed happily may become incompatible.
With ManageWP’s Safe Updates, you can update all your plugins without having to worry about plugin conflicts. If one does occur, then our Safe Updates feature creates a restoration point, so you can easily roll back your changes and troubleshoot the issue without causing downtime for your site.
4. Delete unused plugins
If you’re no longer using a plugin, it’s not enough to simply deactivate it. The tool’s code will still be included in your site’s files, and can therefore still be exploited by hackers. For example, cybercriminals commonly target individual PHP files within a specific plugin.
The ManageWP dashboard includes a tab that lists all your inactive plugins:
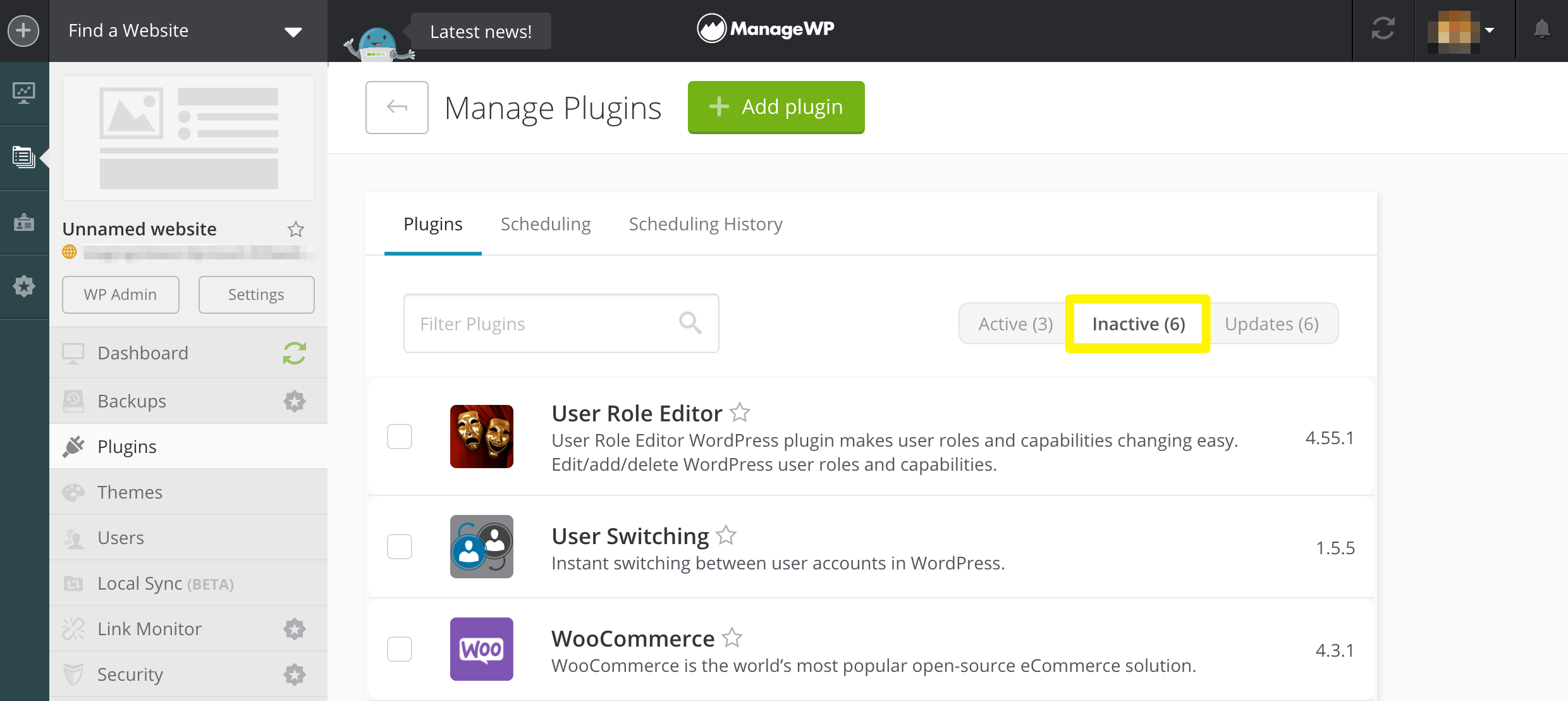
You can easily delete all of these plugins from your site by clicking on Select All > Delete. Alternatively, you can remove a specific one by selecting that plugin’s accompanying checkbox and then clicking on Delete.
5. Stay up-to-date on WordPress security
Hackers create over 350,000 new pieces of malware every single day, so it’s important to follow the latest security developments. There are plenty of websites that post WordPress security updates, but popular sources include Security Boulevard, The Hacker News, and Help New Security. We’d also recommend bookmarking the security section of the official WordPress.org blog.
You should check whether your plugins have websites, blogs, or social media accounts that you can follow. These are often the best places to learn about security issues related to specific products. If a developer has a newsletter or mailing list, then you should consider adding your name to it.
If this all sounds too time-consuming, then we recommend at least following the WPScan WordPress Vulnerability Database. It maintains a publicly-available database of known WordPress Core, theme, and plugin vulnerabilities. You can follow WPScan on Twitter, or sign up for email alerts.
Alternatively, ManageWP Vulnerability Updates feature displays a notification alongside any plugins that have known risks. Checking it daily will keep you in the loop regarding your site’s plugin security.
6. Monitor your website for suspicious behavior
It’s not unusual for developers to avoid publicly announcing a security vulnerability until after they’ve successfully addressed it. This helps limit the amount of damage done, since such notifications could also tip malicious hackers off to opportunities to steal data or install malware. However, your website will remain vulnerable until the issue has been patched.
Avoid waiting for a third party to notify you about an insecure plugin. You can actively monitor your website using tools such as ManageWP’s Security Check. This feature will automatically scan for malware, and monitor whether your site is blacklisted by security-focused services such as Google Safe Browsing and Norton Safe Web. If it discovers a security issue, then it can alert you via email or Slack.
Our Uptime Monitor can also notify you if your site goes down. There are many performance and security issues that can knock your website offline, so downtime doesn’t automatically indicate an issue with your plugins. However, any outage is a serious problem that you should investigate further.
7. Report any plugin security issues
If you discover an issue with one of your plugins, then you should never post about it publicly. Bringing attention to an unpatched security vulnerability gives hackers an opportunity to exploit it. By complaining about it openly, you could be making your website a prime target.
Instead, you should always attempt to contact the plugin’s developer directly. If you downloaded the plugin from the official WordPress Plugin Repository, then you can check its listing for contact details.
If the developer’s contact information isn’t publicly available, then you can check the plugin’s source code. Developers sometimes include contact information there. If you’ve discovered a serious vulnerability and cannot get in touch with the developer, WordPress.org advises you to contact the plugin team instead.
Conclusion
Plugins are one of WordPress’ greatest strengths, but they can also leave your website vulnerable to hackers. By following some straightforward safety precautions, you can still utilize this key component of the platform without endangering your site.
In addition to screening your plugins for quality before installing them, it’s vital that you keep them up-to-date. Always delete unused extensions and monitor your site for signs of security breaches. ManageWP includes several handy features that can help streamline these responsibilities and keep your site safe.
Do you have any questions about plugin security? Let us know in the comments section below!
Image credits: Pexels.

0 Comments